Njrat Red Version Error 404
Njrat Red Version Error 404 the realm of cybersecurity, the emergence of malware represents an ongoing challenge for individuals and organizations alike. Among the myriad of malicious software, one particularly notorious specimen is NJRAT, a remote access Trojan (RAT) that has garnered attention for its potent capabilities and widespread usage in cyberattacks. This essay delves into the intricacies of NJRAT, its origins, functionalities, and the risks it poses to cybersecurity ecosystems globally.
Njrat Red Version Error 404, short for “Njw0rm Remote Access Trojan,” is a piece of malware designed to provide unauthorized remote access to a victim’s computer. Its roots can be traced back to its initial appearance on various online forums, including GitHub, where its source code and subsequent iterations have been shared and modified by cybercriminals. A simple search for terms like “NJRAT download” or “GitHub NJRAT” yields results showcasing its availability and accessibility, contributing to its proliferation.
One of the defining characteristics of Njrat Red Version Error 404 is its versatility, as evidenced by its compatibility with multiple operating systems, including Windows, Android, and even macOS. This adaptability broadens its potential target base, making it a significant threat across diverse devices and platforms. Additionally, NJRAT boasts a range of editions, from the basic 0.7 version to specialized variants like the “Golden Edition,” “Green Edition,” and “Lime Edition,” each with distinct features catering to different cybercriminal objectives.
Njrat Red Version Error 404 modularity and customization options provided by NJRAT’s builder tool enable threat actors to tailor the malware to suit specific attack vectors and objectives. Whether it’s creating command and control traffic or exploiting vulnerabilities in target systems, NJRAT’s capabilities empower malicious actors to execute a myriad of nefarious activities with relative ease. Its use extends beyond mere data theft or system compromise; NJRAT can serve as a potent tool for espionage, surveillance, and even sabotage, amplifying its threat to individuals, businesses, and critical infrastructure.
Despite its sophistication, NJRAT’s proliferation raises concerns about the ethics and legality of its usage. Its deployment often involves exploiting vulnerabilities in software or employing social engineering tactics to deceive unsuspecting users into executing the malware. Once installed, NJRAT operates covertly, evading detection by antivirus software and security measures, exacerbating the challenges of mitigating its impact.
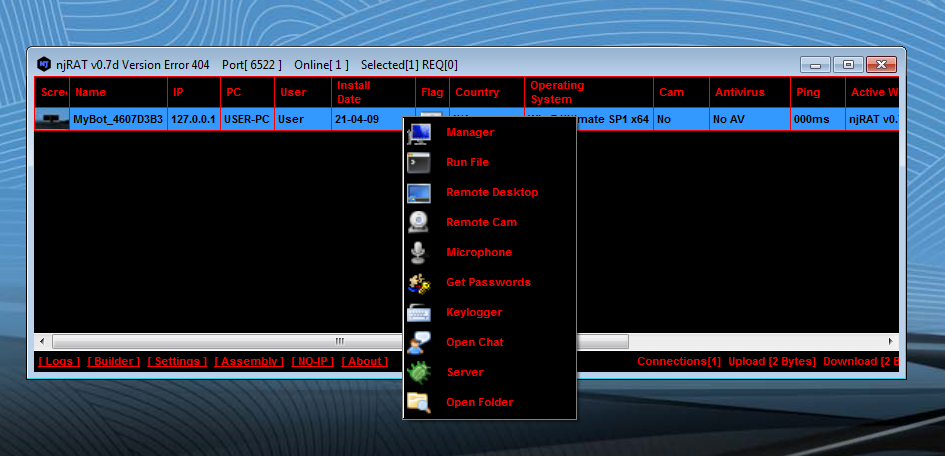
RUN file
Run from script
Run from file
run from link
Remote Desktop
Remote Cam
Keylogger
Saved Password
Micro Phone
Server COntrol
Download Link 1
Mirror Link 2
Download Link 3