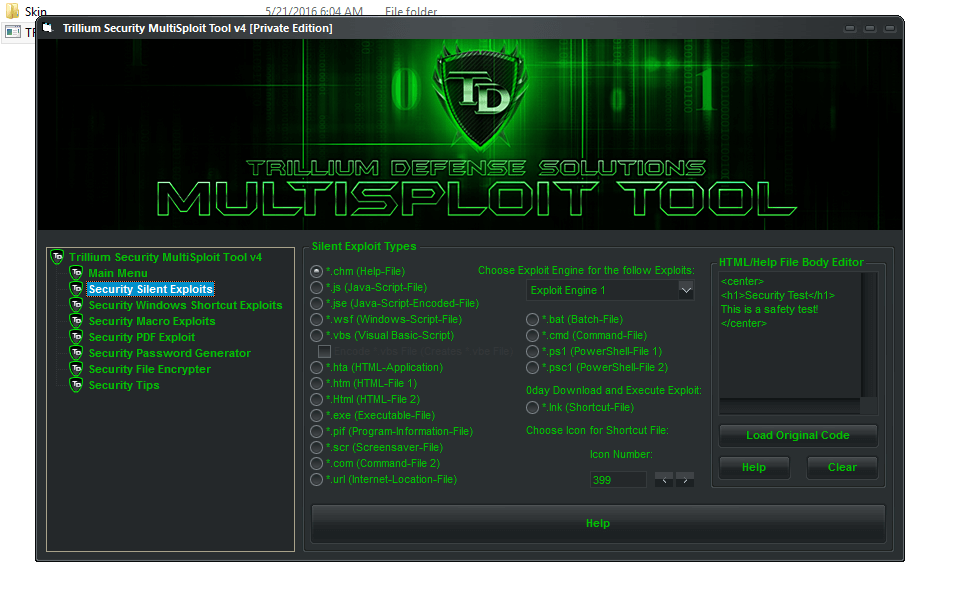
TRILLIUM SECURITY MULTISPLOIT TOOL V4 Private Edition
The Trillium Security Multisploit Tool presents a curious case study in the world of cybersecurity. Versions like v3, v4, and v6 are shrouded in controversy, with iterations like “v6 cracked” raising immediate red flags. While the name suggests a legitimate penetration testing toolkit, a closer look reveals a potential double-edged sword.
Legitimate versions, such as v6.5.3 or v6.5.4, might exist for ethical security professionals to exploit vulnerabilities in controlled environments. However, the abundance of phrases like “cracked” and references to specific versions (v3 being a documented malicious variant) paint a concerning picture.

The Trillium Security Multisploit Tool could be a tool for aspiring hackers, offering a one-stop shop for crafting malware. The ease of use such a tool provides, especially with cracked versions readily available, lowers the barrier to entry for malicious actors. This can lead to a wider range of individuals attempting cyberattacks, potentially increasing the threats faced by businesses and individuals alike.

McAfee’s report on the cracked v3 version highlights this danger. The malware-generating capabilities paired with the ease of distribution pose a significant security risk. Security researchers must constantly adapt to stay ahead of such evolving threats.
The Trillium Security Multisploit Tool serves as a stark reminder of the fine line between legitimate security testing and malicious hacking. While ethical penetration testing is crucial for identifying vulnerabilities, tools like Trillium, when misused, can become weapons in the hands of cybercriminals.

It’s important to note that there is no confirmation of the existence of legitimate versions of the Trillium Security Multisploit Tool. The focus should be on using authorized and well-vetted tools for penetration testing, conducted with proper permissions and within a controlled environment.
Macro Exploit
Windows Shortcut Exploit
Security PDF Exploit
Protection
Uppercase
Lower Case
Custrom String
Base64 Encoding.chm Help Files
.js Java Script file
.Jse Jave script encoded Files
.wsf Windows Script File
.vbs Visual Basic Script
.hta html appication
.htm html file
.Html html file 2
.exe
.pif
.scr
.com
.url
.bat
.cmd
.ps1
.psc1
.link
ICQ:653580170
Whatsapp +79017473945
jabber: [email protected]